Requirements
• Access to a cloud hosting provider (Linode, AWS, DigitalOcean, etc) — that’s literally it.
If you can’t afford cloud servers or prefer hosting locally, you can run this from home — but do so at your own risk. If someone breaks in, it’s on your network.
Setting Up General Ubuntu Server
For this walkthrough, I used Linode because the interface is clean and fast.
This first server will run a listening script that logs:
- Attempted username
- Attempted password
- Attacker IP address
Clone the repository:
git clone <REPO ADDRESS>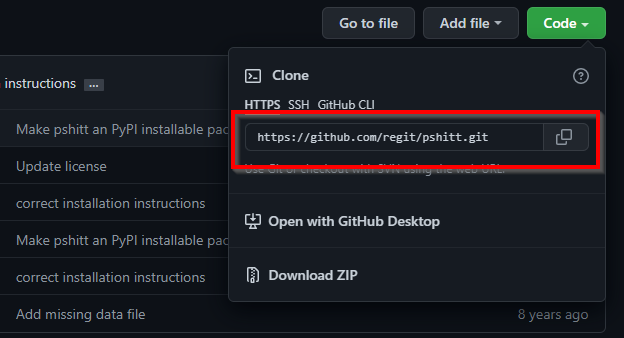
Next, change into the directory you cloned and run the setup script — or manually install dependencies if you prefer.
Before launching anything, update your SSH port in /etc/ssh/sshd_config:
sudo nano /etc/ssh/sshd_config
# change:
Port 22
# to your custom port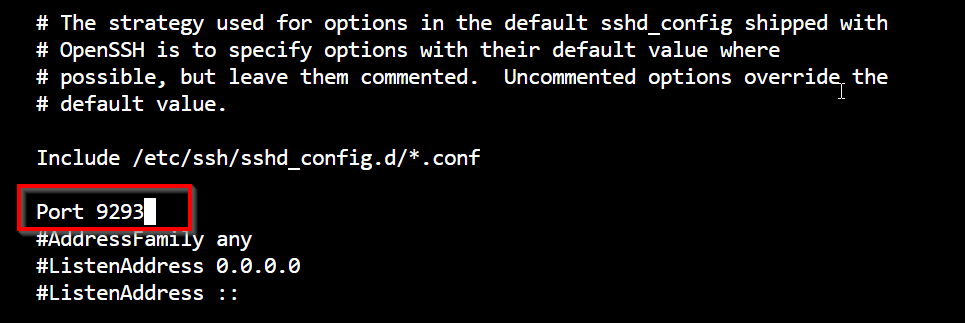
python3 pshitt.py -o passwords.json -p 22Set Up Endless SSH Server
The Endless SSH server setup is very similar:
sudo apt update
git clone <ENDLESS SSH REPO>
sudo apt install build-essential
cd endlessh
make
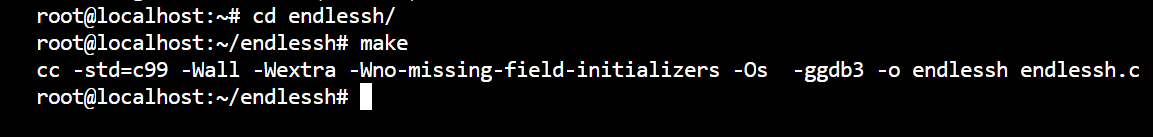
Then run Endless SSH:
./endlessh -p 22 If you want more detailed output, add the -vvv flag.
That’s all you need — your honeypot is live.
If you want me to create a part 2 covering visualization dashboards, attacker heatmaps, or automated reports, let me know.
